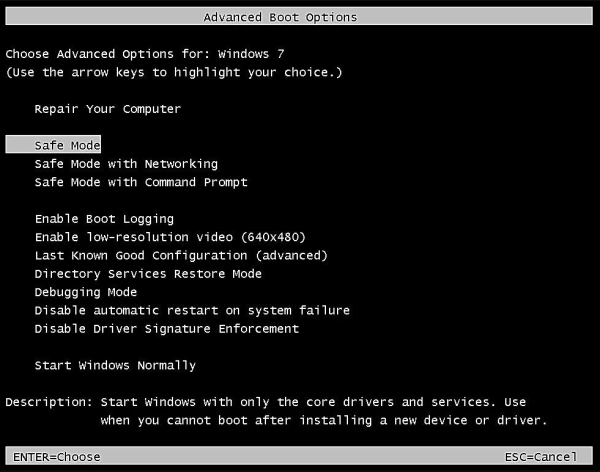
Introduction In this article, we provide an in-depth analysis of the Not-Too-Safe Boot technique, which has been designed to bypass Endpoint Security Solutions like antivirus (AV), endpoint detection and response (EDR) and anti-tampering mechanisms remotely. This method builds on a local execution technique first published in 2007 and later utilized in a real world scenario... Continue Reading →
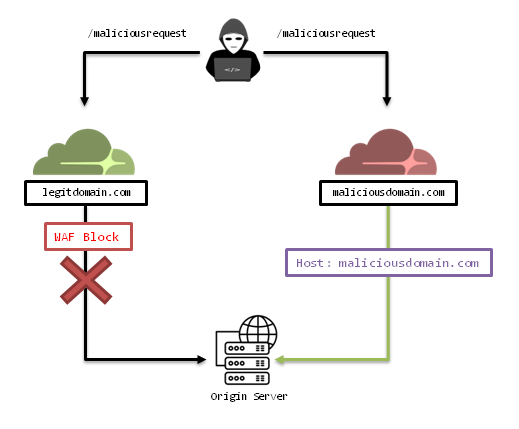
Evilflare: Circumventing Cloudflare’s Protection
Cloudflare is a prominent player in web security and infrastructure, providing essential services like content delivery networks (CDNs), DDoS protection, WAF and more. Despite its robustness, vulnerabilities can still emerge. In this post, we'll delve into the importance of protecting origin servers and explore three attack scenarios that could potentially bypass Cloudflare's defenses. We have... Continue Reading →